Author: ACFE Hawaii
2018 July Luncheon
September 1, 2018
 FBI Special Agent Arnold Laanui discussed Excess of Access, introducing our members
FBI Special Agent Arnold Laanui discussed Excess of Access, introducing our members
to his Urgency-Frequency-Potency model as a means of recognizing and prioritizing
risk. He showed why human fallibility, rather than perceived threats or technical
vulnerability, is the greatest contributor when it comes to intellectual property and
digital information loss.
Dr. Laanui has investigated and researched topics relevant to the digital frontier for
over 20 years. He brings a wide variety of knowledge and accomplishments from his
experience in the FBI. He is Hawaii’s first alumnus of the FBI Honors Program, is an 8-
year veteran of FBI SWAT, a Hawaii TOP COP, and has solved numerous cases ranging
from bank robbery to hacking national defense networks.
2018 May Luncheon
September 1, 2018
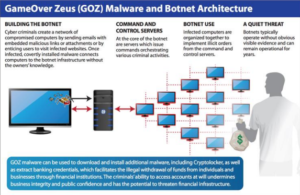
Chuck Lerch, CEO of HiTechHui, shared the fascinating story of Evgeniy Mikhailovich
Bogachev, the man behind GameOver Zeus (GOZ), the distribution system for
CryptoLocker, one of the most notorious ransomware to date. Chuck shared how
ransomware takes control of networks, and what we can all to do protect ourselves
from cyber threats.
2018 March Luncheon
September 1, 2018
We were honored to have two speakers at our March luncheon, discussing Government Corruption and Privacy Relating to Financial Accounts. Both Judge Randal Lee and Chief Special Agent Dan Hanagami have distinguished careers, and have been involved in a number of high-profile, white-collar crime cases in Hawaii over the years.
Government Corruption
The Depart of Attorney General, State of Hawaii has the power to investigate corruption in State and County government personnel; criminal and administrative; State and County law enforcement, criminal and administrative; crimes that focus the State as the primary target; crimes that focus on government employees in their capacity as employees; campaign spending violations; Department of Agriculture prohibited species; Department of Health Recyclables; part of State Law Enforcement Coalition; and address organized takeover of State property.
In the case of a Honolulu police officer who solicited a prostitute, the corruptive matter at hand was the utilization of police powers, equipment, resources, while on duty to commit the act of prostitution; unauthorized use of computer system. The case was investigated in partnership with the FBI, Homeland Security Investigation, and Honolulu Police Department (Professional Standards Office).
Corruption can occur anywhere in the world. Some recent cases outside of Hawaii include:
- The resignation of Japan’s National Tax Agency Commissioner Sagawa Nobuhisa, who was involved in a controversial discount state land sale to private school operator Moritomo Gakuen when he was a senior Ministry of Finance official.
- Mauritian President Ameena Gurib-Fakim, Africa’s only female head of state, is expected to resign after being accused of using a bank card provided by a charity to make personal purchases worth tens of thousands of dollars. The bank card had been provided as part of her work as an unpaid director for the charity.
- In the private sector, Kobe Steel Co. CEO Hiryoa Kawasaki and other top managers after admitting that it falsified inspection data about metal it supplied to makers of planes, cars and other products, to make them appear to meet customer specifications.
Privacy in Financial Accounts
In 1990, the Hawaii Supreme Court adopted a ruling by the U.S. Supreme Court that a defendant did not have a legitimate expectation of privacy in bank records because they were considered records of the bank and not private papers of the account holder. Such records contain information voluntarily conveyed to banks and expoosed to their employees in the ordinary course of business.
Thus, the reasoning went, the depositor takes the risk that the information will be conveyed to the government. That has changed with the advent of the Internet and the Digital Age.
In 2014, in a case where key information was obtained through a store membership card, the Hawaii Supreme Court ruled that the person had an expectation of privacy in a store customer reward card, as it is currently impossible to participate in the economic life of contemporary society without maintaining a bank account. Thus, permitting a police officer to acess these records without judicial control opens the door very real abuses of police power. Those who disclose certain facts to a bank or phone company for a limited business purpose need not assume that this information will be released to other persons for other purposes.
Questions to consider based on legal precedents:
- Does the individual have a legitiamate expectation that such information would not be shared with others?
- Does the information reveal “intimate details of a person’s life”?
- Did the individual release the information to a third party to obtain a necessary service?
- Were there realistic alternatives to disclose the information, i.e. would such disclosure jeopardize an individual’s sense of security?
- If information is deemed to be protected, the police must obtain a warrant before conducting such searches.
2018 January Luncheon
September 1, 2018
IRS Special Agent Mark MacPherson from the IRS Criminal Investigations (CI) Unit discussed Current Tax Fraud Trends with our members at the January luncheon. Compliance with the tax laws in the United States relies heavily on self-assessments of what tax is owed. This is called voluntary compliance. When individuals and corporations make deliberate decisions to not comply with the law, they face the possibility of a civil audit or criminal investigation which could result in prosecution and possible jail time. Publicity of these convictions provides a deterrent effect that enhances voluntary compliance.
The highest-level government official charged with tax evasion was Spiro Agnew, the 39th Vice President of the United States from 1969 to 1973. More recently, former Trump campaign chairman Paul Manafort was indicted for nine criminal counts, including money laundering and tax fraud.
Since its inception in 1919 to the present, the conviction rate for Federal tax prosecutions has never fallen below 90 percent. As noted on the unit’s website, “If the motive of the crime is money, chances are Criminal Investigation special agents are involved in tracking the money, from the crime to the criminal.” Along with their financial investigative skills, special agents use specialized forensic technology to recover financial data that may have been encrypted, password protected, or hidden by other electronic means. For more information, check out their website: https://www.irs.gov/compliance/criminal-investigation/criminal-enforcement
2017 November Luncheon
December 29, 2017
Michael Miranda shared his insights on Cybersecurity for the Modern Hawaii Professional: Mobile, Cloud and Home Offices in his capacity as principal consultant with Spartix at our November luncheon. He is also an Assistant Professor of Information Security at the University of Hawaiʻi – West Oʻahu, which has been designated a National Center of Academic Excellence in Cyber Defense Education by the National Security Agency and the U.S. Department of Homeland Security and recently served as the Director of Information Security for Hawaiian Telcom.
He showed that accessing a single, seemingly harmless site like cnn.com inadvertently also opens the door to potentially hundreds of other domains, from ads to tracking info to sharing sites like Instagram or Twitter, introducing significant business risks. He advises those with home offices to segregate business information, with a separate router (and separate devices in general) as a best practice to prevent possible malware from family devices to affect your business.
With cloud services, it pays to assess or audit the service provider for appropriate certifications, use of encryption, employee background checks and data centers’ physical location. The location could present potential legal jurisdiction issues that could impact your access to your data. It is also important to ask how to take the data with you if you decide to leave that particular provider. While it is tempting to use free cloud services, paying for these services means provides certain guarantees detailed within service level agreements.
2017 September Luncheon
December 29, 2017
Our members learned about U.S. Customs and Border Protection and its duties related to fraud, through presentations by Watch Commander George Minamishin and Supervisory CBP Officer Scott Kikkawa.
With more than 60,000 employees, U.S. Customs and Border Protection, CBP, is one of the world’s largest law enforcement organizations and is charged with keeping terrorists and their weapons out of the U.S. while facilitating lawful international travel and trade. As the United States’ first unified border entity, CBP takes a comprehensive approach to border management and control, combining customs, immigration, border security, and agricultural protection into one coordinated and supportive activity. The men and women of CBP are responsible for enforcing hundreds of U.S. laws and regulations. On a typical day, CBP welcomes nearly one million visitors, screens more than 67,000 cargo containers, arrests more than 1,100 individuals, and seizes nearly 6 tons of illicit drugs. Annually, CBP facilitates an average of more than $3 trillion in legitimate trade while enforcing U.S. trade laws.
In Hawaii, ports of entry in Hawaii include: Hilo, Honolulu, Honolulu International Airport, Kahului, Kona and Nawiliwili-Port Allen. Hawaii also functions as part of a liaison group for carriers in the Asia-Pacific region, training airline personnel to spot potential fraudsters, and provide pre-flight intelligence to CBP if for example they have a high-risk passenger suspected of having fake travel documents. CBP estimates that intercepting one suspected passenger, before he or she gets on a plane, saves the U.S. government $15,000 to $100,000 per passenger, since it can take up to a month to process their case after they arrive in the country.
Fraud Prevention Officers are primarily document examiners, verifying security features for travel documents, which as similar to currency. Officer Kikkawa showed examples of counterfeit attempts and how they were discovered.
When document become too difficult to replicate, in some cases fraudsters find it easier to use someone else’s documentation as their own. Officer Kikkawa tested our members’ facial recognition skills with a game called “Real vs. Imposter”. He showed photos on travel documents, alongside photos of people at the port of entry who may or may not have been the same person. His pro tip was to look at parts of the face – e.g. left ear, bridge of the nose – instead of trying to evaluate each face as a unified entity.
For more information, check out these pages:
- Snapshot of CBP operations
https://www.cbp.gov/sites/default/files/assets/documents/2017-Jun/CBP-Snapshot-06012017.pdf
- A Typical Day in Fiscal Year 2016:
2017 July Luncheon
September 3, 2017

For the past nine years Justin Geer has worked as an Immigration Officer at the Honolulu Field Office of the USCIS, an agency of the Department of Homeland Security. Justin works to enhance the integrity of the legal immigration system by helping to lead agency efforts to identify threats to national security and public safety, detect and combat immigration benefit fraud, and remove systematic and other vulnerabilities. Prior to his work with USCIS, Justin worked for a non-profit in the Chicago area that specialized in refugee resettlement and immigration legal services. U.S. Citizenship and Immigration Services (USCIS) created FDNS in 2004 in order to strengthen USCIS’s efforts to ensure immigration benefits are not granted to individuals who pose a threat to national security or public safety, or who seek to defraud our immigration system. In 2010, FDNS was promoted to a Directorate which elevated the profile of this work within USCIS, brought about operational improvements, and enhanced the integration of the FDNS mission in all facets of the agency’s work. Today FDNS continues to lead the USCIS effort to ensure the integrity of the nation’s immigration benefits processes.
FDNS’s primary mission is to determine whether individuals or organizations filing for immigration benefits pose a threat to national security, public safety, or the integrity of the nation’s legal immigration system. FDNS officers are located in every USCIS Center, District, Field, and Asylum Office. FDNS officers are also located in other government agencies. Supporting the USCIS mission, FDNS’s objective is to enhance USCIS’s effectiveness and efficiency in detecting and removing known and suspected fraud from the application process, thus promoting the efficient processing of legitimate applications and petitions. FDNS officers resolve background check information and other concerns that surface during the processing of immigration benefit applications and petitions. Resolution often requires communication with law enforcement or intelligence agencies to make sure that the information is relevant to the applicant or petitioner at hand and, if so, whether the information would have an impact on eligibility for the benefit.
FDNS officers also perform checks of USCIS databases and public information, as well as other administrative inquiries, to verify information provided on, and in support of, applications and petitions. Administrative inquiries may include:
• Performance of fraud assessments – FDNS officers engage in fraud assessments (including Benefit Fraud and Compliance Assessments) to determine the types and volumes of fraud in certain immigration benefits programs;
• Compliance Reviews – Systematic reviews of certain types of applications or petitions to ensure the integrity of the immigration benefits system, and
• Targeted site visits – Inquiries conducted in cases where fraud is suspected. FDNS uses the Fraud Detection and National Security Data System (FDNS-DS) to identify fraud and track potential patterns. USCIS has formed a partnership with Immigration and Customs Enforcement (ICE), in which FDNS pursues administrative inquiries into most application and petition fraud, while ICE conducts criminal investigations into major fraud conspiracies.
FDNS also conducts Benefit Fraud and Compliance Assessments to identify the types and volumes of fraud and develop mitigation strategies to deter and disrupt fraud. In July 2009, FDNS implemented the Administrative Site Visit and Verification Program (ASVVP) to conduct unannounced site inspections to verify information contained in certain visa petitions. USCIS provides petitioners and their representatives of record (if any) an opportunity to review and address the information before denying or revoking an approved petition based on information obtained during a site inspection
2017 May Luncheon
July 10, 2017
Kupuna Alert Partners
Our members were treated to several speakers in June, courtesy of Kupuna Alert Partners, a multi-agency partnership presentation covering Medicare Fraud Prevention, Securities Fraud Prevention and Prescription Drug Misuse.
Charlie Pang, Dept. of Public Safety, Narcotics Enforcement Division
He talked about the dangers of prescription drug abuse or misuse, such as someone taking medications not prescribed for them or combining different drugs to enhance the effect of another substance, such as alcohol.
Approximately 6.8 million Americans abuse prescription drugs, typically from friends or family members. Fortunately, there is a national takeback program, in which Hawaii participates. For information the Hawaii Medication Take Back Program, call (808) 837-8470. He noted that pharmacies, hospitals and clinics are not allowed to take back drugs, so contact the program to ensure safe disposal. As much as 3,200 lbs. have been collected and disposed of at H-Power Plant, which burns trash at high temperatures and ensures destruction. Disposing of drugs in the trash or toilet leads to drugs in the landfill or sewage systems, which do not break down and can affect reef fish.
To help protect against prescription drug abuse or misuse, document all medications you are taking and create five copies: (1) for your primary physician, (2) pharmacy, (3) family, (4) your wallet, (5) your refrigerator. Keep track of your medications, use one pharmacy to fill all prescriptions, secure your medications and if in doubt about any of your medications, ask your pharmacist.
Leolyn Sugue-Anderson, DCCA Securities Enforcement Branch
She covered the Top 5 scams in Hawaii, which were:
- Impostor fraud – e.g. impersonating someone from the IRS
- Fake prizes, sweepstakes, lotteries
- Telephone, mobile scams – e.g. claims that someone got into your account, requesting account information
- Banks and lenders – similar to above
- Debt collection – e.g. claiming your home is facing mortgage foreclosure
Scams on the rise include:
- Advance fees – requesting a fee to enable you to collect on returns from an investment or prize
- Romance scams – targeting divorced, widowers
- Grandparents – claiming a call from a “relative” who is stranded or hurt, requesting that they send money. Personal details may have been stolen or bought from other sources.
Protect against scams by not responding to calls from unfamiliar numbers, check financial statements for any unfamiliar transactions, and monitor your credit through free sites like www.annualcreditreport.com.
Laurie Paleka, Senior Medicare Patrol
Senior Medicare Patrols (SMPs) empower and assist Medicare beneficiaries, their families, and caregivers to prevent, detect, and report health care fraud, errors, and abuse through outreach, counseling, and education. SMPs are grant-funded projects of the federal U.S. Administration for Community Living (ACL), U.S. Department of Health and Human Services (HHS). Its basic message is
- PROTECT – guard Medicare and Social Security numbers, don’t let anyone borrow
- DETECT – review medical statements the same way as a credit card or bank statement
- REPORT – if you notice anything unusual, to SMP at (808) 586-7281 or (800) 296-9422
Valerie Mariano, Dept. of the Attorney General, Community and Crime Prevention Branch
Hawaii Revised Statutes 485A covers regulations pertaining to the registration of securities, broker-dealer, agents, investment adviser representatives. When evaluating investment opportunities, check if they are properly registered by calling 1-877-447-22667. To check on financial advisers, search their histories on https://brokercheck.finra.org.
2017 March Luncheon
May 1, 2017
Our luncheon speaker was one of our own board members, Margie Sasaki, who currently works as a consultant for the Blue Cross Blue Shield Association’s Special Investigation Unit. Prior to going into business for herself, she worked at HMSA for 27 years, spending the last 16 years in management in the Special Investigation Department.
At our March luncheon, she talked about Medical Fraud Waste and Abuse, which affects all of us. The National Health Care Anti-Fraud Association (NHCAA) estimates that this category totals tens of billions of dollars a year, and we are all paying for it.
Some examples of the typical types of fraud:
- Billing for services that were never rendered
- May involve identity fraud
- A patient went to a new dentist to find that her old dentist had actually not capped her teeth even though she was billed for it
- A patient reported not obtaining services that were billed, claiming that an insurance card was stolen by a brother, who apparently used it at a doctor’s office. In that case, the doctor was the victim.
- Billing for more expensive services or procedures (also known as “upcoding”)
- Insurance companies “code” certain conditions to determine the appropriate level of service. A higher code generally means a medical need for a higher level of service.
- Insurance companies routinely use algorithms to monitor these codes
- Comparisons of doctors over time or by peer group can help detect potential fraud through unnecessary services to generate insurance payments
- In one case, a doctor who was not a cardiologist purchased an echocardiogram for his office, the increased billing for these types of tests by 70 percent in a single year
- In some cases, doctors receive kickbacks for testing referrals
- Misrepresentation of non-covered treatments as medically necessary to receive coverage
- Cosmetic procedures like nose jobs are usually diagnosed for coverage as deviated septum
- Falsifying patient diagnoses to justify tests or procedures
▪ Anesthesia for colonoscopies are only covered for high risk patients but some will add a COPD diagnosis just to get coverage
▪ The consequences include potentially getting turned down for life insurance if that information is accessed during routine reviews for coverage
She also showed various videos of mainland schemes, ranging from “runners” who get paid for each patient they bring in, rounding up non-English speakers so they could bill for services that were not in fact rendered or were unnecessary. Many schemes ran in the millions of dollars and caused serious harm to their patients. Because Hawaii is not a big market, we don’t often hear of these large cases here, but last year at least $9 million was recovered at HMSA. Opioid abuse, for example, strikes everyone, from ages 12 to 86 years old.
Margie’s advice:
- Be informed of your diagnoses for your own health, and those of your loved ones
- Keep good medical records and review your bills
- Treat your insurance card like a credit card. Call your insurance company immediately if it’s lost.
- Be on alert for elder abuse: some people go door to door and tell seniors they work for the government in order to to get their insurance card information.
- Read your policy, especially the explanation of benefits
If you see any type of fraud, call your insurance company immediately. Other places to call include the Hawaii State Insurance Commissioner and Dept. Commerce and Consumer Affairs.
2016 November Luncheon
January 4, 2017
The U.S. Probation Office monitors those who are released from federal prison. Derek Kim is one of 24 federal probation officers here in the state and supervises federal offenders on probation or supervised release. He has been with U.S. Probation for 18 years and supervises offenders convicted of sophisticated “white–collar” offenses, including Ponzi schemes, tax offenses, embezzlement, money laundering, wire/mail fraud, bank fraud, and aggravated identity theft.
Many of his offenders have been chief financial officers, accountants, company presidents, and managers of government and private agencies or businesses, as well as programs that receive federal funds. “Supervision” could last anywhere from 3 years to a lifetime, depending on the crimes. This includes home inspections, drug tests, surveillance and searches.
In addition, the federal government pays for counseling and other services needed for rehabilitation. Derek notes that, oddly enough, white collar criminals tend to be remorseful when they are caught, because they had convinced themselves that they are no different from their clients, aside from the problems that drove them to commit their crimes.
As a probation officer, Derek can recommend that they go back to prison and start over if they don’t pass muster. Because of this, he sees his job as determining why they committed the crime, how they did it, and how he can help them keep from doing it again.
Based on his experience, there are four drivers for those who commit white collar crimes: Drug Habit, Financial Problems, Feeling of Entitlement and Greed (Predators). Common methods of crime, rationalization, risk of recidivism, and monitoring areas for each are as follows:
|
||||||||||||||||||||||||||||||||||||||||||